Transmitting keys is a foundational risk to security, as they can be harvested and decrypted later. This is a step-by-step description of how Qrypt’s independent key generation technology provides long-lasting protection against data attacks.
Transmitting keys is the risk. Cryptographically relevant quantum computers will break today’s RSA and ECC encryption. NIST PQC algorithms are new and have yet to show resilience over time. When keys are broken, everything an attacker intercepted and stored can be exposed. In the long term, today’s data is not secure.
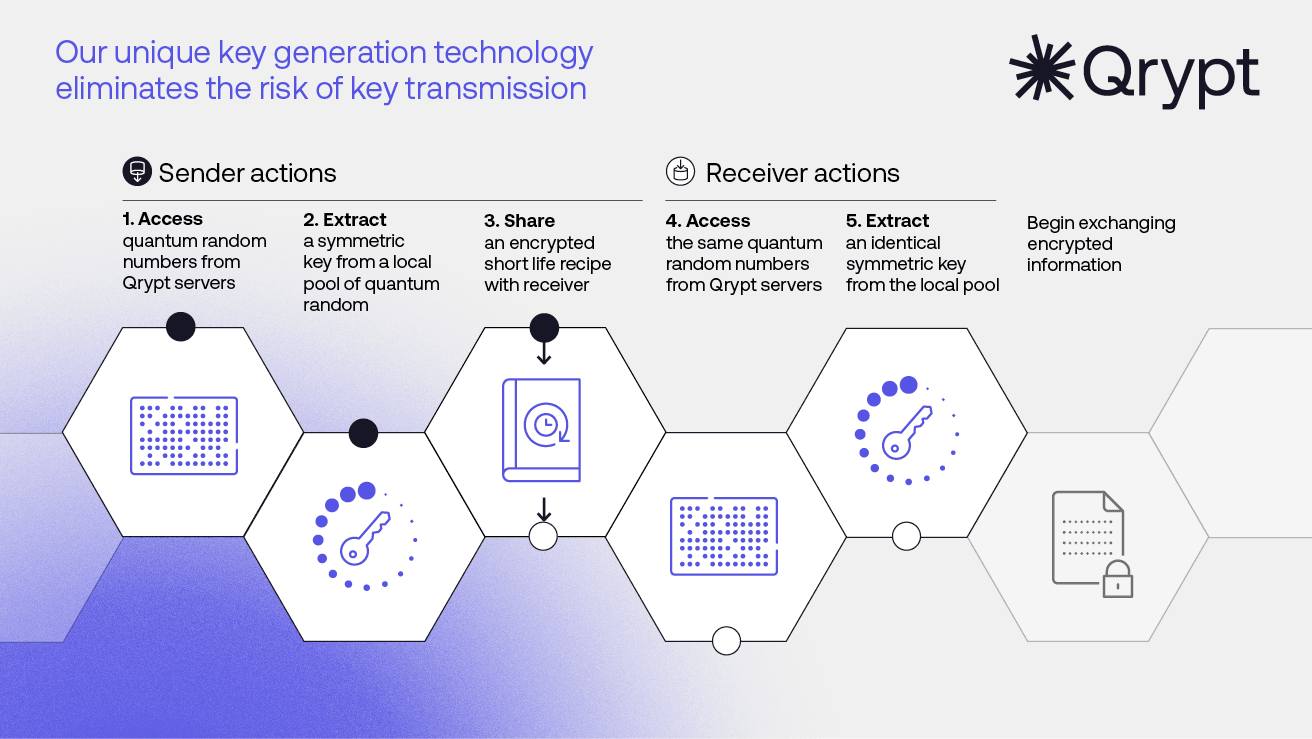
Qrypt Quantum Key Generation works by sharing a recipe to enable parties to each create the same key.
It starts with true quantum random numbers. Qrypt Quantum Entropy servers provide unique pools of random numbers that are the resource used to create keys. The Qrypt Quantum Security SDK accesses the servers and locally creates a symmetric encryption key or one-time pad.
A recipe is then created that includes server and key generation parameters. This short-life recipe is then shared with recipients.
Short-term assumptions for long-term privacy
This recipe is sent over any channel that can maintain data security for at least an hour. RSA, ECC, and NIST PQC all meet this requirement.
Why does this work? An attacker must intercept the recipe and decrypt it in under an hour. The attack fails if the recipe can’t be decrypted before random number pools are shredded.
Long-term privacy and security
Once you generate keys without transmission, you achieve long-term security. Even if a technique is invented to break encryption in less than an hour, previously transmitted data isn’t at risk as keys were not transmitted or harvested. You update future recipe transmissions to use new encryption sustaining your long-term security.
With Qrypt, by assuming short-term security you get long-term privacy and security. Since encryption keys have never gone across the wire, your data is never at risk from a harvest and decrypt later attack.
For the details behind this technology, you can read the original publication by our Chief Cryptographer Yevgeniy Dodis “Doubly-Affine Extractors, and their Applications.”
Also, sign up for our newsletter on our home page or contact our sales team at info@qrypt.com to learn more.