While quantum computing poses a significant challenge to our encrypted world, the pivotal point of concern is not the quantum computer itself but the key transmission process susceptible to quantum threats. This key transmission process, a fundamental aspect of secure digital communication, is now under threat. This risk is not a distant one; it’s already upon us.
The primary quantum threat, the “Harvest Now, Decrypt Later” (HNDL) strategy, is already underway. Adversaries are accumulating encrypted data today, waiting for quantum capabilities to crack it open. And the cornerstone of this strategy is exploiting the weakness in key transmission.
This imminent risk of symmetric key exposure, facilitated through quantum-vulnerable asymmetric exchange, is the epicenter of the quantum crisis. The threat is monumental, real, and urgent. We need to act now.
The Fundamentals of Asymmetric Key Exchange
In every digital communication, there is a sender and a recipient. In fact, often it isn’t just one sender and one recipient, instead, there can be multiple senders and recipients interacting simultaneously.
These can be humans, machines, Internet of Things devices, transmission towers, or even a network of multiple endpoints. Irrespective of the use case, the scenario remains the same.
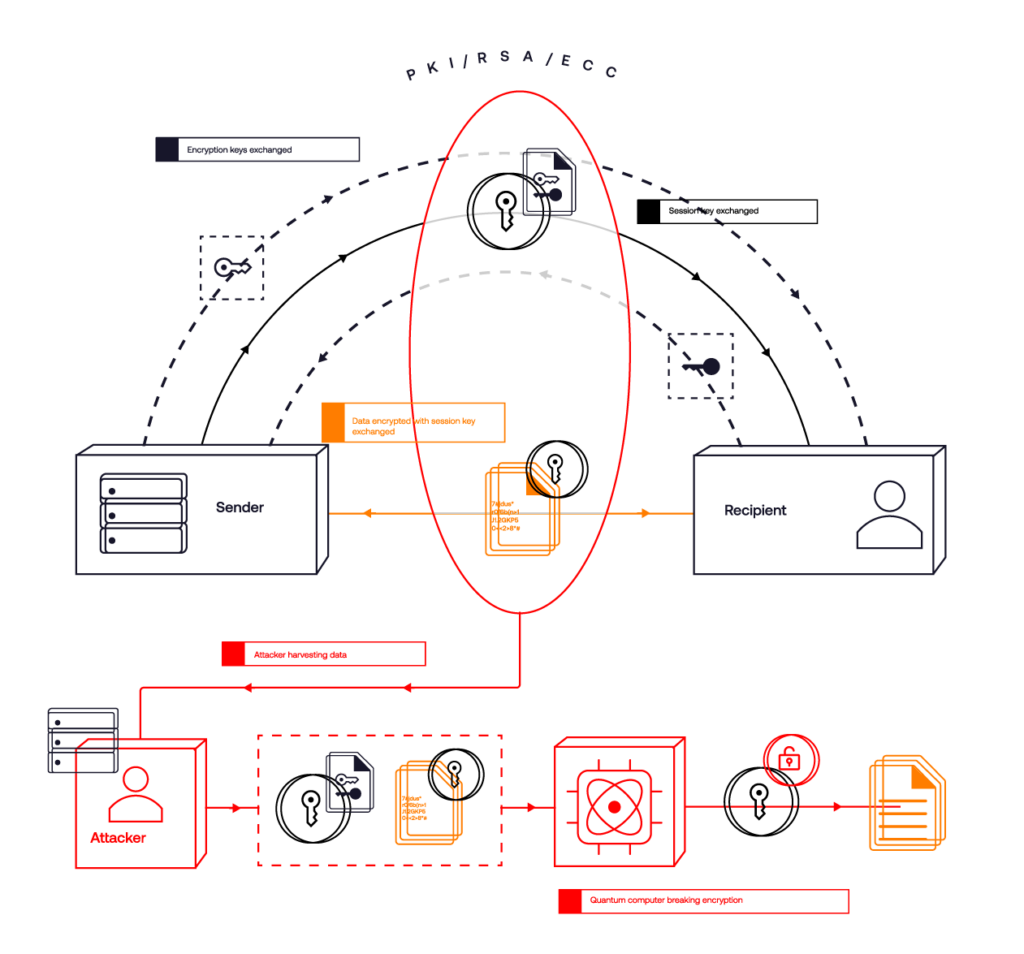
The transmission process begins with a public key infrastructure (PKI) exchange (we’ll skip handshakes and initial connectivity for brevity). This exchange establishes an asymmetric channel between the sender and the recipient. In this channel, the sender and recipient exchange a symmetric key, which is used to secure data or communications during the session.
This asymmetric exchange process relies on algorithms like RSA or ECC, algorithms that are not quantum-safe or secure long-term. Next, the key to understanding quantum risk is understanding what is transmitted through this asymmetric PKI channel.
Symmetric Key Encryption
After establishing the asymmetric channel, the communication process advances to the exchange of a symmetric key. This symmetric key plays a fundamental role in the secure communication between sender and recipient.
These keys are the lynchpin of secure digital communication, as they are used to encrypt the data exchanged during a session. Their vulnerability, therefore, poses a grave threat to our data security.
This symmetric key, commonly an Advanced Encryption Standard (AES) key, is transferred over the initially created asymmetric channel. Compared to asymmetric encryption, a symmetric key is preferable due to the computational efficiency of symmetric encryption, especially for large amounts of data.
The sender and recipient now share an identical symmetric key, which will be used to encrypt and decrypt the data transmitted between them. It’s worth noting that asymmetric encryption’s primary role is not to encrypt the actual data communication but to secure the exchange of this symmetric key, also referred to as the session key.
AES is a robust and widely trusted encryption method, serving as a cornerstone in modern cybersecurity. However, its longevity in a quantum-threatened future is closely tied to the security of the key transmission process. While AES itself remains a stalwart defense, its effectiveness can be undermined if the method of sharing or transmitting its keys is compromised by quantum threats. Essentially, even the strongest encryption can be rendered vulnerable if the process of key exchange is susceptible to future quantum attacks.
This brings us to a turning point in the narrative: the quantum threat and its implications on data security. In the next section, we’ll discuss how quantum computing disrupts the status quo of encryption key transmission.
Symmetric Key Capture IS the Quantum Risk
The real crux of the quantum risk is the vulnerability of the symmetric key used to encrypt and decrypt most of our data.
Malicious actors already employ the “Harvest Now, Decrypt Later” (HNDL) strategy. In this scenario, threat actors capture and store the entire asymmetric encrypted data transmission, which includes both the symmetric key and the data encrypted by it, awaiting the day a quantum computer can decrypt it..
Before we dive deeper into this alarming reality, let’s first grasp the concept of HNDL. The premise is simple: adversaries are actively harvesting encrypted data today with the intention of decrypting it later when advancements in quantum computing become available. This strategy doesn’t discriminate between different types of data. All data is targeted and captured, including the seemingly trivial bits. When parsed by future machine learning (ML) and artificial intelligence (AI) technologies, these small pieces of information can paint a complete and intimate picture, providing valuable insights into individuals, businesses, or even government activities. It’s akin to the method of signal intelligence (SIGINT), where bits and pieces of information are assembled to reveal a larger narrative.
When evaluating the captured data, the encrypted symmetric key emerges as the ultimate prize. During a secure session, the symmetric key, essential for data encryption, is protected solely by the at-risk asymmetric encrypted channel. This symmetric key, along with the data it encrypts, is what threat actors are harvesting today. Quantum computers of the future will crack the asymmetric encryption protecting this symmetric key. Once they can access the symmetric key, they can decrypt the corresponding data collected today and decrypt future data transmitted using the same key.
The Inevitable Breach
When quantum computers can run Shor’s algorithm at scale, they can break the RSA and ECC encryption that secures the asymmetric key exchange.
This breach will expose the symmetric key and all the encrypted data in the session.
With the symmetric key revealed, an attacker will decrypt all past and future data encrypted with that key as long as it remains unchanged.
This scenario is not a distant threat. Data is being harvested by adversaries today. They are counting on future quantum computing capabilities to crack the encryption and unlock the value of harvested data.
The consequences of such an attack would be unparalleled. Beyond the immediate compromise of personal identification details, financial transactions, intellectual property, and state secrets, there’s a broader implication. The first entity, be it a nation or organization, to achieve quantum decryption capabilities might silently leverage this advantage, potentially leading to an unseen and monumental shift in power and wealth. This covert wealth transfer could be the largest in human history, reshaping global dynamics. Such a profound potential impact underscores the urgency of addressing quantum threats now, not later.
Conclusion
Our exploration shows that the quantum risk is not merely a distant or abstract threat but an ongoing challenge in the present digital landscape. The crux of the vulnerability lies in the transmission of encryption keys, a pivotal aspect of our cybersecurity framework. Recognizing this is the initial step towards addressing and mitigating quantum risks.
As we navigate the complexities of this transition to a quantum-secure eco-system, it’s crucial to explore and implement potential solutions proactively:
1. Cryptographic Inventory: Begin by conducting a comprehensive cryptographic inventory. Understand where your keys are stored, how they’re managed, and where they originate and end. Identify usage of quantum-at-risk algorithms. This foundational step provides clarity on the current state of your cryptographic defenses.
2. Secure Key Transmissions: Evaluate opportunities to either eliminate key transmissions or quantum-secure them immediately. Solutions like Qrypt’s Quantum Key Generation and Quantum Secure Tunnel offer innovative ways to address the vulnerabilities associated with key transmissions, ensuring that data remains secure even in the face of quantum threats.
3. Preparation for NIST PQC: With the looming quantum era, it’s essential to migrate to NIST Post-Quantum Cryptography standards. These standards provide a robust framework for quantum-resistant cryptographic methods, ensuring that organizations are equipped to handle the challenges posed by quantum computing.
In the rapidly evolving realm of quantum cryptography, a balanced approach that combines adherence to established standards with the integration of pioneering solutions will be paramount. This ensures a resilient, future-ready cryptographic defense, adeptly addressing the distinct challenges of the quantum epoch. As a global community, we can shape a secure digital future.